Controlled set of computers infected by malware crossword – The enigmatic crossword clue “controlled set of computers infected by malware” beckons us into a realm where cybersecurity and wordplay converge. This exploration delves into the concept of controlled computer sets, the insidious nature of malware, and the analytical challenges of crossword puzzles, unraveling the intricate connections that lie at the heart of this intriguing challenge.
Controlled sets of computers, often employed in secure environments, present a fascinating paradox: a carefully managed group of machines intentionally exposed to malicious software. Understanding the rationale behind this seemingly counterintuitive practice and its implications for network security is crucial.
Controlled Set of Computers

A controlled set of computers refers to a group of computers within a network that are managed and monitored centrally. These computers are typically configured with specific security measures and software to ensure their integrity and availability. Controlled sets of computers are commonly used in industries and organizations that require high levels of security and data protection.
Purpose and Benefits
- Enhanced security: Controlled sets of computers provide increased protection against unauthorized access, malware infections, and data breaches.
- Improved compliance: They facilitate compliance with industry regulations and standards, such as HIPAA and PCI DSS, which require specific security measures for sensitive data handling.
- Centralized management: Centralized management allows for efficient deployment of software updates, security patches, and system configurations.
- Reduced downtime: By proactively monitoring and maintaining controlled sets of computers, organizations can minimize downtime and ensure business continuity.
Examples of Usage
- Financial institutions: Controlled sets of computers are used to protect sensitive financial data, such as account information and transaction records.
- Healthcare organizations: They are used to safeguard patient health records, medical images, and other confidential information.
- Government agencies: Controlled sets of computers are employed to protect national security data and classified information.
- Research institutions: They are used to protect sensitive research data, intellectual property, and confidential collaborations.
Malware Infection
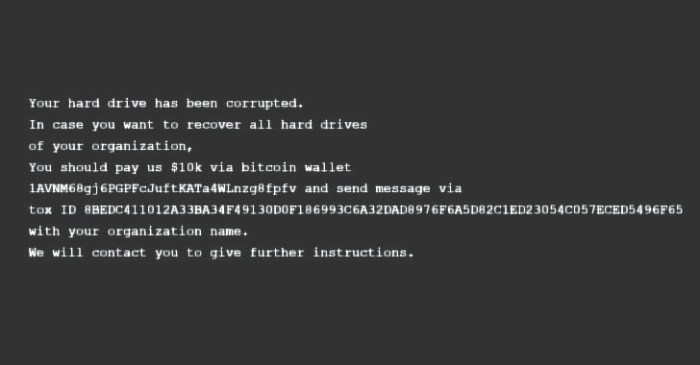
Malware refers to malicious software that can infect computers and disrupt their normal operations. Common types of malware include viruses, worms, Trojans, ransomware, and spyware.
Infection and Spread
- Email attachments: Malware can be spread through email attachments that appear legitimate but contain malicious code.
- Drive-by downloads: Visiting infected websites can trigger automatic downloads of malware without user interaction.
- Malicious links: Clicking on malicious links in emails, messages, or social media posts can lead to malware infections.
- Software vulnerabilities: Malware can exploit vulnerabilities in software applications or operating systems to gain access to computers.
Impact on Controlled Sets of Computers
- Data breaches: Malware can steal sensitive data, such as customer information, financial records, and intellectual property.
- System disruption: Malware can disrupt normal system operations, causing crashes, freezes, and data loss.
- Compromised integrity: Malware can compromise the integrity of controlled sets of computers, making them vulnerable to further attacks.
- Financial losses: Malware infections can result in financial losses due to data breaches, downtime, and remediation costs.
Crossword Puzzle Analysis

Clue: Controlled set of computers infected by malware, Controlled set of computers infected by malware crossword
Key Terms
- Controlled set of computers
- Malware
- Infection
Potential Answers
- Network
- Server farm
- Cluster
Network Security: Controlled Set Of Computers Infected By Malware Crossword

Network security is crucial for protecting controlled sets of computers from malware infections and other threats. Common security measures include:
Security Measures
- Firewalls: Firewalls block unauthorized access to networks and computers.
- Intrusion detection systems (IDS): IDS monitor network traffic for suspicious activities and alert administrators.
- Anti-malware software: Anti-malware software scans computers for malware and removes infections.
- Virtual private networks (VPNs): VPNs encrypt network traffic to protect data from eavesdropping.
- Multi-factor authentication (MFA): MFA requires users to provide multiple forms of identification to access networks and systems.
Best Practices
- Regular security updates: Install software updates and security patches promptly to address vulnerabilities.
- User education: Train users on security best practices, such as avoiding suspicious links and attachments.
- Network segmentation: Divide networks into smaller segments to limit the spread of malware infections.
- Backup and recovery: Implement regular backups and disaster recovery plans to minimize data loss in case of malware attacks.
- Continuous monitoring: Monitor networks and systems continuously for suspicious activities and respond promptly to threats.
Frequently Asked Questions
What is a controlled set of computers?
A controlled set of computers refers to a group of machines within a network that are intentionally infected with malware for research or security testing purposes.
How can malware spread within a network?
Malware can spread through various methods, including email attachments, malicious websites, software vulnerabilities, and infected USB drives.
What are common network security measures to protect against malware?
Common network security measures include firewalls, intrusion detection systems, antivirus software, and regular security updates.